Improving the Physical Security Industry: Process Improvement Methods
Ollencio D'SouzaMost Physical Security Industry blogs make a case for why other industries need Physical Security, but the future of the physical security industry relies on adapting to process improvement methods if it wants to stay relevant and develop a third eye that looks inward to improving business processes and harnessing the concepts of Continuous Improvement.
Successful businesses use Business Process Mapping (BPM) tools to visualise, document, communicate, analyse, improve, simulate and execute both their operations and a cost optimised workflow.
At times, they hire consultants to create a BPM model for the internal use of their executives so the management team can collaborate to build an optimised process map which eventually defines the DNA of the organisation.
The physical security industry would gain much from understanding workflow and process mapping because it makes it easier for the industry to understand the cause and effect of any introduced process or technology on operational effectiveness.
It also helps to mesh these benefits into over-arching corporate objectives and goals. Process mapping is an opportunity to understand current practices and then develop more effective business operations and management practices in the future.
Consultants have a major role to play in the visual mapping of core business activities. A consultant’s analysis of what happens against what is supposed to happen operationally when proposing changes, additions or integrations, would go a long way to determining the positive or negative impact on the company’s commercial results.
When delivering a tailor made specification to an organisation, consultants would be able to present their ideas and suggestions on technology upgrades or integration and even prove the efficacy of their suggestions by simulating the workflow and staffing requirements, thus enabling management to visualise the process and quantify its effect on the bottom line.
The facility management industry is forced to work within product driven silos, delivering manpower, technology, installation and services to meet customer needs and would do better if they mapped and understood the impact of technology or manpower recommendations on their current operational work flow. A technology shopping list in specifications which include proprietary product families, integration with other non physical security systems and functions that are, sometimes, a paradigm shift to the status quo, would require some modelling analysis to ensure it would reach a cost effective equilibrium.
Using BPM to Analyse Workflows in System Integration Scenarios
This article will introduce Business Process Management as a useful and effective tool to analyse workflows in system integration scenarios.
For example, 'company A' has on board legacy technology collected over many years as they expanded and grew their operations. Typical overall workflow mapping of the deployment is shown in this workflow drawing...
Figure 1: Typical Legacy Workflow
(Figure 1. Tasks with a + are sub processes that flesh out each step). The workflow overview map separates technology as distinct from the human aspects in a typical legacy operational environment.
Technology has evolved over many years to automatically perform mundane tasks, based on industry experiences, using embedding logic in systems and devices (e.g. supervision of sensor status) in the field. The verified data is then delivered to the human decision making pool where certain rules of operation/workflow apply (such as escalation or off line review, remote supervision, etc) To understand why it is necessary to have a business process mapping etiquette in any operational environment, one has to understand that;
Step-1: we are dealing with human beings who need to be given well thought out priorities and processes to perform at their best, so risks are minimised and/or mitigated, cost effectively.
Step-2: we need to reduce the impact of product driving operations (operators tend to be trained on a particular system – and find it difficult to operate on a different system even though the principles of security operations remain the same). The only way to remedy the situation is to understand the workflow required to best deal with the security and safety scenarios and then introduce the technology to follow the plan. By documenting and sticking to a suitable event, action and response process, setup and programming of the system will operate in sync with the agreed operational plan.
Step-3: make it easy to improve a workflow process by being able to model changes before implementing them so as not to disrupt existing workflow (i.e. requirement for re-training).
The difference between a Flow Chart and a Business Process Map (BPM) is distinct (Figure 2);
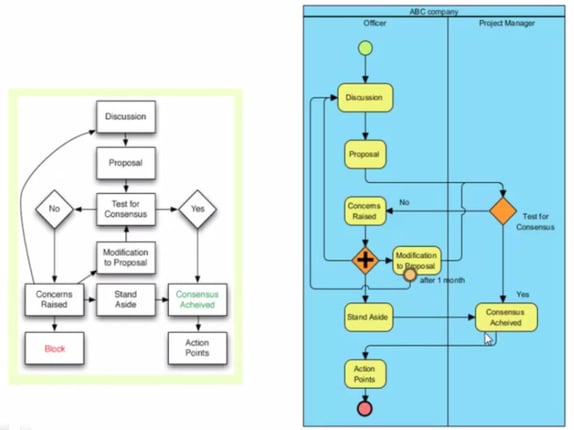 Figure 2: Difference Between Flowchart and BPM
Figure 2: Difference Between Flowchart and BPM
1. It identifies who triggers a process start
2. It allocates who is doing what in pools/lanes identifying departments that are given the responsibility to perform that function.
3. It nominates who makes the decision and the sequence in which it is made
4. It identifies dependencies, either in the decision tree or in the activity process that must be completed before the process moves ahead, thereby overcoming 'holes' in the process.
5. It clearly shows when one process ends and the other process begins.
6. It can be used to simulate, flow, costs and to optimise and test out different operational scenarios.
What happens when existing technology (legacy) systems are upgraded or integrated with new technology driven functions? Such as adding CCTV to Intruder, Access Control, fire or BMS – etc?
The BPM (Figure-3) maps the functionality of two coupled environments – the technology (hardware) and the human.
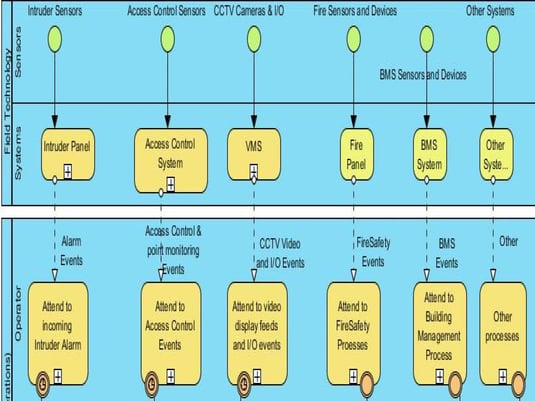
Figure 3: Technology, 'Hardware' and 'Human'
Where the technology has been enhanced with logic to automatically perform some of the basic functions which were done by the 'humans' in times gone by but are now automated by firmware at the edge, we need to accept that categorising this technology functional area and giving it an identity is just as important as placing an operator (to perform a specific process/task) into the system. For example – to prevent false alarms reaching the human operator, clever logic is used to filter out the noise and deliver a credible alert/alarm/event message to the command and control centre (like a trained operator who knows what to respond to and what to ignore).
As automation becomes common place in a big data environment where there is tremendous growth in the application of sensors of many kinds, SMART analysis technology is increasingly used to provide early intervention to detect and correct common issues. These automated sub- processes need to be embedded in our process map so we can recognise them as required tasks that help improve the overall efficacy of the solution. We need to identify these automated processes embedded into the hardware or software, as distinct process/task/sub processes that need to be included in our business process mapping.
Technology and Functional Integration:
A customer or a consultant may react to a serious incident by calling for an upgrade of the technology. Many scenarios come to mind;
1. Calls to ditch the current supplier/product because it did not perform and go for some other brand!
2. Add CCTV/Intruder/Access Control/BMS/Fire/EWIS/ VoIP, etc to the mix
3. Add advanced technology such as two way audio, biometrics, remote viewing and response, etc
It is reasonably easy to imagine and develop a shopping list of product and functions that would help. But it is tough to visualise the process which failed because no one has analysed and documented the scenario earlier. Would we allow the same thing to happen with an upgrade without using BPM to understand what really happened and develop the workflow to stop it happening again? Questions that can be asked are;
1. Was the process adequate to respond to the event/alarm and capture/respond in a manner that helped mitigate the risk?
2. What was the weakness in the process?
3. How could the process be modified to deliver the outcomes required if this event/alarm occurred again?
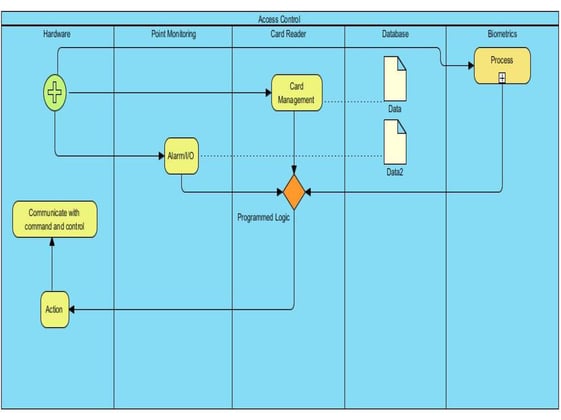
Figure 4: Access Control Sub-process Overview
It is not the technology but the process which determines if the desired outcomes are deliverable. After the process is established, technology to aid the process should be evaluated so that it facilitates the outcomes.
In a legacy environment where independent technologies were the norm and operators were required to jump from one user interface to the other – because the technology required it – the workflow did not matter whether the operator has to go through multiple control points (like keyboards and monitors) to determine if the event/alarm actually was of concern. The true cost of this kind of an operation, in human and financial terms could never be estimated because there were no tools to simulate the exercise and map the workflow.
Today, integration is a word too easily bandied about. The question is, does integration...
1. Reduce the number of interfaces that an operator has to get to confirm the threat?
2. Increase the number of ways an event/alarm is detected and delivered to the operator for an assessment and final decision?
3. Improve the repository and access to relevant information from all the subsystems (technology) deployed in essence to get a multifaceted perspective on the event/alarm or in short, create better situational awareness?
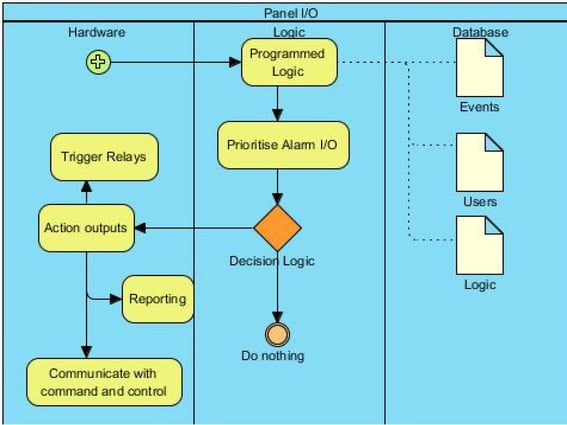
Figure 5: Intruder Alarm Hardware (Panel Logic)
If you review the technology platforms in use today (Figure 4, 5, 7), integration could occur;
A) At the Technology (hardware) level pool (say between the intruder and CCTV, or Access and CCTV, etc) making it difficult for a system independent collaborative approach because the alarm trigger from one subsystem triggers another subsystem- so how could actionable information be made available to the operational staff, when the decision of what is required is made at the hardware level between two subsystems? (Figure 6)
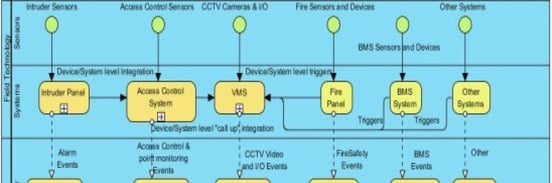 Figure 6: Limited Hardware/System Level Integration
Figure 6: Limited Hardware/System Level Integration
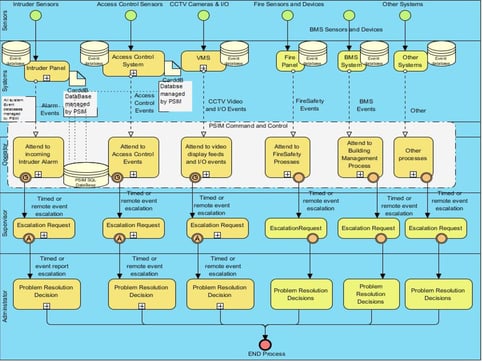
Figure 8: CCTV System Sub Process
B) At the Command and Control level (PSIM) where data is collected from any device on the system to deliver a comprehensive package of relevant information that would support a credible reasoned approach to the threat and a confidence level that would enable the most appropriate response be delivered. (Figure 7)
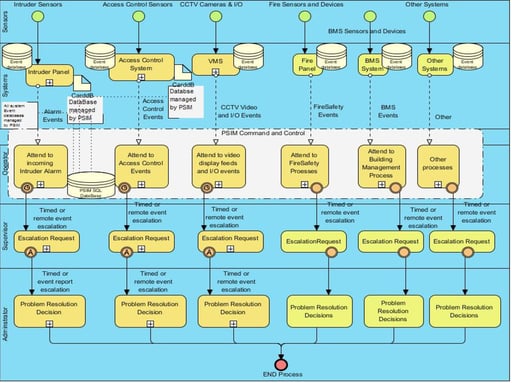
Figure 7: PSIM Delivered 'Integration'
Estimating Costs:
Throughout the business process mapping exercise, values are attributed to an element and every time the process has to use this element – it accrues a cost. In the simulation of the process (and one can take different paths that relate to choices or decision to check what each path costs) if a process ends up being repeated or stopped for a missing decision the consequences are both operational (time exit – use timed events to escalate or pass a halted process to another process) and the accrued cost results in an estimate of what it would cost not having the resource at that process point.
The Final Decision Making Process:
When considering a Business Process Mapping exercise, consider a good software tool as a starting point. Develop the workflow that best mimics the business process currently in place. Define the new Workflow based on what is required to be achieved in terms of operational speed and cost outcomes then define the technology which will assist the process.
This means that one needs to leave the technology choices towards the end so it is possible to establish what functional technology elements or configuration would suit the mapped process. Which means the technology should work in line with the BPM process not vice versa! Data (triggers from sensors) is not actionable information so this must be passed through sub-processes (i.e. appropriate logic filters set out in the business process mapping exercise delivered by configurable and programmable devices) to determine what would best help improve situation awareness, credible alarm/alerts and the responses most appropriate to comply with the goals and objectives of the organisation.
More information
We hope you enjoyed this article by Ollencio D'Souza. If you are interested in the potential improvement benefits of a Business Process Management System, take a look at the 4 Critical Steps to Finding a Business Management System or alternatively, if you need help in quantifying the real benefits of business improvement, then take a look at the  , which will help to analyse the best way forward for your business improvement project...
, which will help to analyse the best way forward for your business improvement project...
Related Articles:
Business Process Management for Real People
Understanding Business Process Management: A Beginner's Guide
10 Reasons Why BPM is Important for Your Business Improvement Strategy
Written by Ollencio D'Souza
Ollencio D'Souza is the Managing Director of TechnologyCare, which focuses on making technology work for customers. Ollencio is a specialist in Computers, Networking, IP Video (analogue and digital), System architecture, Electronic design and diagnostics using electronic instrumentation, Development of in house integrated solutions using core OEM PSI and Video & Audio analytic technology. IoT Design and Construct (MQTT, LoRAWAN) and Business Process Modelling
